In an era where businesses rely heavily on Software as a Service (SaaS) solutions, ensuring the security of your data has never been more critical.
Whether you’re an IT professional, business owner, executive, or cybersecurity enthusiast, understanding the steps to protect your valuable data in the SaaS environment is essential. In this article, we present the ultimate SaaS Security checklist.
Let’s dive in.

Step 1: Access Your Current Controls and Data Security
The heart of your SaaS security strategy lies in protecting your data. Intellectual property, customer data, and employee information are all pieces of the sensitive data puzzle that organizations must protect for business continuity.
Some of the security measures to consider for data protection include:
Authentication
Authentication is the most basic security control an organization can implement. It dictates who can access its networks, systems, and data.
Basic authentication requires the use of a valid user ID and password to access the organization’s cloud-based applications.
It doesn’t end here. Two-factor authentication and multi-factor authentication add an extra layer of security to your cloud applications by requiring users to answer a security question or provide a unique code before gaining access.
Single-sign-on (SSO) and role-based access control also ensure that users have limited accounts and access only what they need to perform their tasks.
Secure protocols, such as role-based access control and least-privilege access, ensure that only authorized personnel can view certain data sets, reducing the risk of internal and external threats compromising sensitive information.
Data Encryption
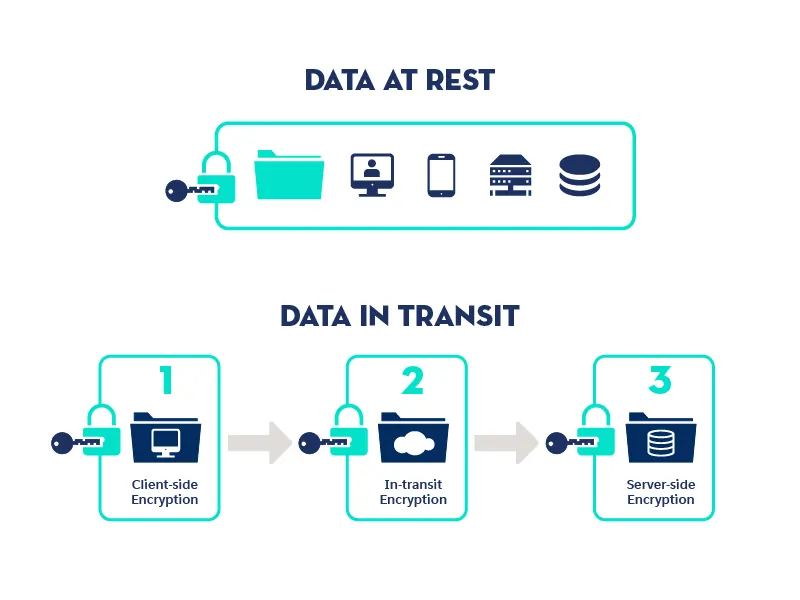
Most data security issues affect data in transit (during communication) or at rest (in storage). Data encryption ensures that the data is unreadable by unauthorized users.
SSL/TLS and AES are the common data encryption techniques used to maintain data privacy in transit and at rest, respectively.
By ensuring robust data encryption methods, you significantly reduce the risk of data breaches and ensure that your sensitive information remains safe, both during transmission and storage.
Data Retention and Deletion
Depending on the data you process using SaaS platforms, you must have a data retention and deletion policy as part of your SaaS security checklist.
Why? This policy helps get your entire team on the same page about the following:
- How to properly delete and discard data while also adhering to regulatory requirements
- Different classes of the data you should hold
- Which data to keep or discard
- How long to keep the data
Data Back-up and Recovery
Your SaaS security checklist should also include a data backup and recovery policy to guide you on how and where to back up data.
Data loss is an affliction that affects even the most prepared organizations, whether due to human error or a technical failure.
Your checklist must cover the backup frequency (preferably within minutes), multiple backup locations, a data recovery plan, compliance, and security of the backup.
Pro-tip: Do you store your data in the cloud? Creating a comprehensive s3 backup strategy could save your SaaS from financial and reputational damage.
Step 2: Understand Your Regulatory Compliance Requirements
SaaS applications often handle sensitive customer data, and different industries have their own specific regulations to adhere to. Make sure your SaaS environment complies with relevant laws and standards.
The common compliance standards include:
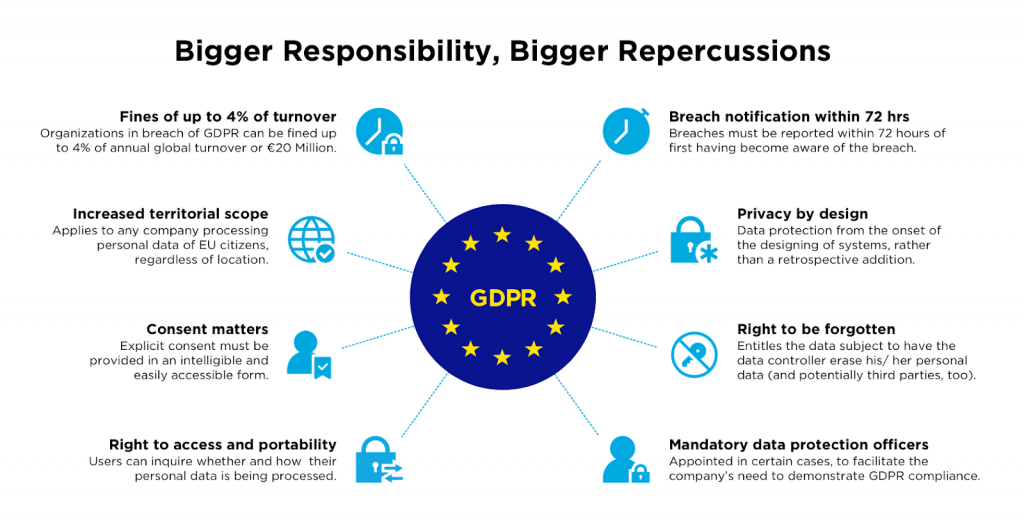
General Data Protection Regulation (GDPR)
GDPR stipulates how organizations can collect and process data from members of the EU, whether the organizations are in or outside the EU. You must ensure that your SaaS security checklist encompasses the principles of the GDPR.
Payment Card Industry Data Security Standard (PCI DSS)
If your organization deals with credit card transactions, you must ensure your infrastructure and cybersecurity practices protect cardholders’ information.
This standard requires that you have a secure network that you regularly evaluate for potential threats, have a strong access management policy, and maintain an information security policy.
Systems and Organization Controls (SOC)
The SOC framework provides the criteria for managing customer data through five reference points, including:
- The protection of personal and sensitive information from unauthorized users
- The protection of confidential information during access, use, and storage
- The integrity of processing systems to ensure they operate as intended
- Availability of the system to allow stakeholders to complete their tasks
- The security of the system from unauthorized access
- NIST 800-53 Risk Management Framework
The National Institute of Standards and Technology Risk Management Framework provides a checklist for assessing IT risks arising from the supply chain. Following these requirements is key in assessing SaaS vendors and endpoints across the supply chain.
Plus, it can help save you millions of dollars per year.
ISO 27000
ISO 27000 outlines the standards for information security management systems that organizations worldwide should implement to ensure the security of their:
- Third-party information
- Financial information
- Intellectual property
- Employee data
Step 3: Conduct Employee Education on Security Risks
It’s almost a proverbial saying in cybersecurity circles that the human factor continues to be a big security concern.
Social engineering attacks, for example, rely on human weaknesses to succeed. With such cyber attacks, unauthorized users can gain access to the most secure applications.
According to the Verizon 2023 Data Breach Investigations Report, internal actors contributed to 30% of all breaches in North America. These internal actors include employees, thus highlighting the importance of ongoing security awareness programs.
Employee education goes beyond sending a cybersecurity memo. It’s an ongoing and elaborate process that’s equally important.
Employee cybersecurity awareness should cover the following:
- Behaviors that create cybersecurity risks, such as using public Wi-Fi or unsecured personal devices to access work-related applications.
- Best cybersecurity practices, such as creating strong passwords, including the organization’s password policy.
- Common cybersecurity risks such as malware, phishing, and hardware loss that exploit human errors.
- Using multi-factor authentication.
You must also include a human-factor cybersecurity evaluation framework to continuously assess the cybersecurity threats the workforce presents.
This framework should include metrics and evaluation criteria for different threats. It must also assess employee behavior when they interact with the organization’s IT infrastructure.
Step 4: Don’t Skimp on Vendor Evaluation
The Accellion FTA data breach highlights the need for your security checklist to include a vendor security evaluation framework.
A security weakness in third parties can affect your organizations when these vendors access your networks, systems, or servers.
To minimize such threats, you must continuously monitor third parties and assess the security risks they pose to your organization.
Since it’s often difficult to control what third-party vendors do, your protection initiatives should begin at the vendor selection stage:
- Adopt an access management system that limits third-party vendors’ access to your organization’s data. With such access management, threat actors have limited access to your data should a breach occur.
- Go for vendors that implement good cybersecurity practices, including compliance with regulatory requirements.
- Conduct regular security audits of third-party vendors to assess their risk profile.
- Implement thorough policies on data sharing, access, storage, and transfer.
Step 5: Invest in IT Infrastructure Security
Your SaaS security checklist is incomplete if it fails to include a provision for IT infrastructure security. This umbrella covers your organization’s software, hardware, devices, cloud resources, and other technology assets that can be a potential source of security vulnerabilities.
Some of the common threats to IT infrastructure include:
- Malware and ransomware
- Theft or vandalism
- Phishing attacks
- Bots
Here’s a table summarizing the most common threats, according to Verizon.
Cloud infrastructure security should address the following layers:
- Physical assets
- Applications
- Networks
- Data
IT infrastructure security can include various actions, including:
- Conducting regular penetration tests and security tests to check for vulnerabilities
- Removal of unused and unnecessary software and devices
- Using secure protocols and channels for communication
- Implementing and analyzing access controls regularly
- Using firewalls and ensuring they’re well-configured
- Implementing intrusion detection systems
- Using antivirus and anti-malware tools
- Applying security patches regularly
- Deleting dormant accounts
- Using encryption
As part of your IT infrastructure security, you should conduct regular security audits to check for security concerns and existing security holes.
Step 6: Run a Vulnerability Assessment and Threat Detection
The cybersecurity threat landscape is always evolving. Therefore, a SaaS security checklist must provide a framework for keeping up with these threats and ensuring continued SaaS application security.
Vulnerability assessment involves identifying the security weaknesses (and their origins) within your organization and the level of risk they pose from low to high.
Vulnerability assessments can be automated but should include regular manual checkups like penetration testing.
It also helps to have the fresh eyes of a security vendor evaluate your IT systems and people for security threats that internal security teams may miss.
Threat detection works on identifying elusive security threats that often pass the safeguards organizations put in place.
For example, a robust vulnerability and threat detection system can conduct employee monitoring to identify suspicious or risky user behavior.
The vulnerability assessment and threat detection system must provide a system for dealing with these threats and fixing any vulnerabilities before malicious actors can take advantage of them.
Step 7: Create a Disaster Response Plan
Business executives aren’t new to risk management initiatives. They take various measures to protect themselves and their business, such as opening a special bank account or choosing a business model that minimizes liability.
Likewise, a disaster response plan serves as a risk management plan focusing on cybersecurity.
The Cybersecurity & Infrastructure Security Agency (CASA) recommends a three-pronged approach to dealing with cybersecurity threats. The first step includes all the activities undertaken before a cyberattack.
These are often preventative measures such as cybersecurity staff training, developing an incident response plan, conducting simulation drills, identifying an external security vendor, and selecting your incident response team.
The second step covers the actions the organization takes during a cyberattack incident. These activities include mobilizing the incidence response team, communicating with stakeholders about the attack, and mitigating the effects of the cyberattack.
The final step involves a retrospective cyber incident analysis to evaluate the cyberattack. From this retrospective analysis, your organization should update its:
- Security protocols
- Procedures
- Training
- Policies
The goal? To prevent similar incidents from occurring.
Bottom Line
A SaaS security checklist provides a comprehensive framework for safeguarding your data and applications in a cloud-based environment.
By following the steps discussed above, you’re well on your way to establishing a robust security posture that protects against threats, complies with regulations, and protects data continuity.
Remember that SaaS security is an ongoing process that requires attention and adaptation. Cybersecurity threats evolve, and your security measures should evolve with them.
So, regular training, testing, and monitoring are key to maintaining a secure SaaS environment.























Leave a comment!