All businesses across all industries have different software for different purposes. Whether it be operating system software or application software, any business that uses a computer uses software – which means they need to consider software security.
This article aims to shed light on the importance of software security, outline the components of a robust security framework, and provide a step-by-step guide to bolstering your software’s defense mechanisms. Through a structured approach, you’ll gain the necessary knowledge and strategies to fortify your business against the escalating threat of cyber-attacks.

Understanding the Importance of Software Security
Software provides potential access points for malicious actors and cyber criminals to infiltrate an organization’s sensitive data and procedures. With the global cost of cybercrime expected to reach $8 trillion in 2023, the need for robust software security measures to safeguard against financial loss and reputational damage has never been more paramount.
The Rising Trend of Cyber Attacks
With increased digitalization, data breaches are becoming increasingly common, with 70% of businesses worldwide falling victim to a ransomware attack in 2022. If a business’s data and sensitive information become exposed in a cyber attack, it can cause significant financial and reputational harm.
Because a single breach can reveal customer data, financial records, and other confidential, valuable information, businesses are lucrative targets for cybercriminals. They can either obtain business data and exploit it, sell it, or encrypt vital business data and demand a ransom for its release.
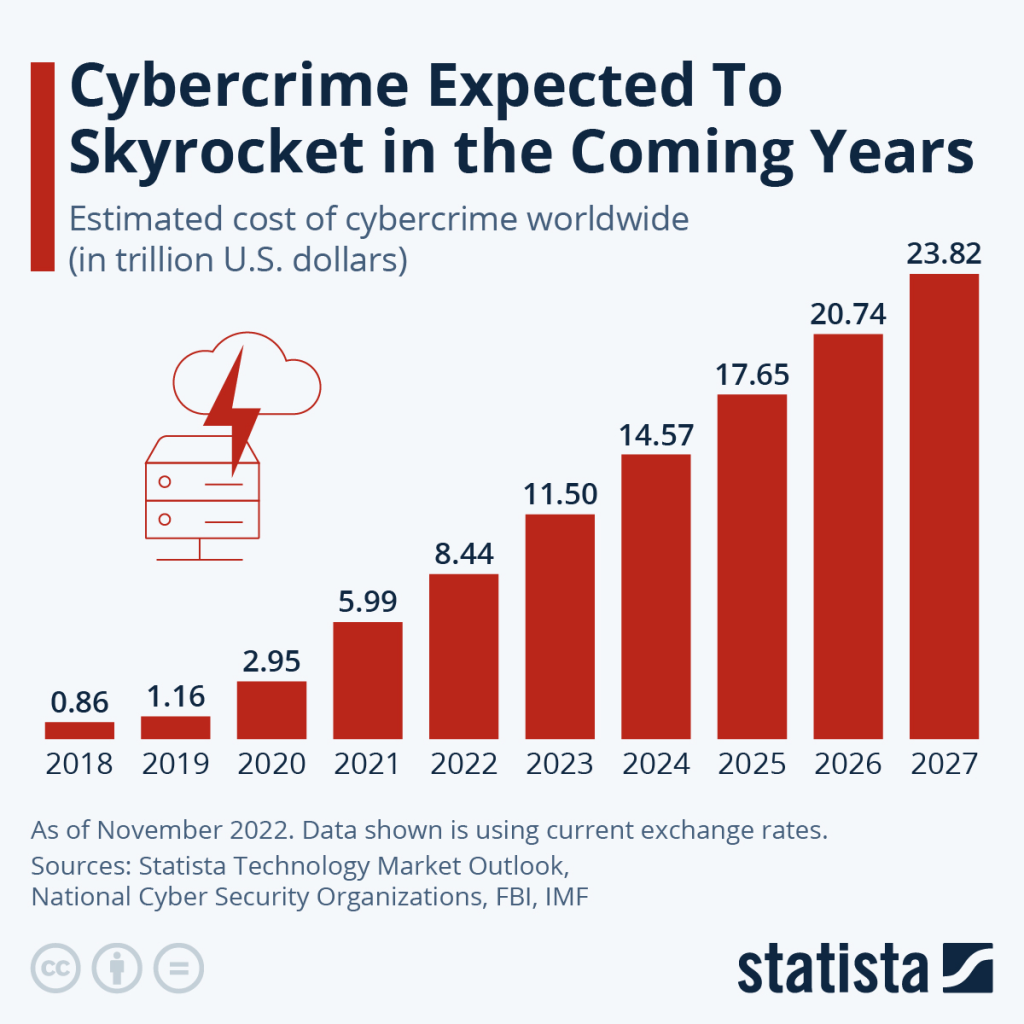
Consequences of Inadequate Software Security
The financial losses from cyber attacks can be substantial, with the average cost of a data breach in the US costing $9.48 million in 2023.
These losses encompass not only the immediate costs of addressing the breach but also the long-term costs of customer reimbursement and legal compliance. Moreover, the damage to a company’s reputation can be long-lasting, with customers losing trust in the ability of the business to protect their data.
Legal repercussions are another significant concern. Failing to comply with data protection laws and regulations can result in hefty fines and legal penalties, ranging from $100 to $1 million per violation, adding to the already significant financial burden.
As such, these risks associated with inadequate software security clearly underline the importance of investing in robust cybersecurity measures to ensure the ongoing safety and integrity of business operations and customer data.
Elements of Robust Software Security
Software security isn’t a one-size-fits-all scenario. Different businesses require different security measures. Having a robust software security means implementing a variety of measures to ensure a well-rounded defense against potential cyber threats.
Firewalls and Anti-Malware Tools
Firewalls are like your security guards, which monitor the traffic between your network and the outside world. They come in different types, tailored to varying security needs, but their general purpose is to identify potential malicious actors and block them from accessing your software and systems.
Anti-malware tools are the next step, as they help detect and remove malicious software that might have made it past your firewall and into your system. Firewalls and anti-malware software are absolutely essential and fundamental in any software security plan.
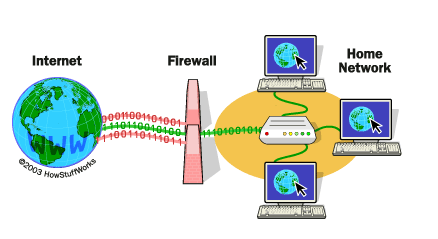
Source: Comodo
Encryption and Authentication
Encryption helps keep sensitive data safe by scrambling it into a code, while authentication verifies the identity of anyone accessing the system. Multi-factor authentication (MFA) is an important security protocol that enhances access security, making it easier to manage who gets access to what (think Google authenticator, for example).
Secure Coding Practices
Secure coding is about building your software right from the ground up with security in mind. It involves reviewing code for potential vulnerabilities and adhering to best practices that reduce the chances of security flaws. Using secure coding best practices is a very valuable, preemptive approach to software security, one which can prevent many issues further down the line once the software has been deployed and is in use.
Cloud Security
Cloud security is about safeguarding your data and applications in the cloud. It involves using tools and procedures to control access, protect data, and ensure compliance with security policies when using cloud computing.

Source: Stefanini
Compliance and Regulatory Adherence
Staying compliant with legal and industry-specific regulations is crucial to avoid fines and legal troubles. Furthermore, staying compliant with governing data protection policies will help take your software security to an industry-standard level, making it more robust than many other of your peer businesses.
Implementing Cyber Armor: A Step-by-Step Guide
Taking steps towards robust software security is a methodical process. It begins with an assessment of the current security posture, followed by selecting appropriate security solutions, training the team, and implementing security controls. Each stage is crucial to building a strong defense against cyber threats.
1. Assess Your Current Security Posture
The first step in elevating your software security is to identify existing vulnerabilities in your current security setup.
Start this by using vulnerability scanning tools to automate the identification of weaknesses across your network and software, and also use the services of an ethical hacking provider to simulate cyber attacks. This helps you see your system from the perspective of a cybercriminal, and will also show you where your system is weak.
Next, you can conduct risk assessments to help analyze and quantify these risks, while analyzing historical incident data will provide insights into past security incidents to identify patterns and areas for improvement.
From here, a gap analysis comparing the current and desired security posture will highlight areas that need attention, and measuring your organization or business against industry standards will help you understand where your security measures stand relative to compliance regulations and other businesses.
Once you’ve clearly understood your starting security posture, then proceed by setting clear and measurable security improvement goals to guide your efforts moving forward, and to choosing the necessary software security solutions for business.
2. Select the Right Security Solutions
Start by evaluating the features and capabilities of any security solutions to obtain a clear picture of what each offers. Customer reviews and case studies will help you better understand the experiences that other businesses had with each security solution and will be valuable assets in your decision-making process.
Customized security solutions tailored to specific business needs can provide enhanced protection, which is where engaging the services of security solution providers can help in understanding the customization options available.
When selecting your cybersecurity solutions and software security protocols, budgeting for cybersecurity is crucial. Make sure you understand the total cost of ownership of security solutions, and allocate resources for future security investments is a recommended step to ensure continuous improvement in your security posture.
3. Train and Educate Your Team
Security training is crucial as it helps in addressing common security misconceptions.
First, role-specific training will ensure that your team is well-equipped to handle security-related tasks, while developing a security-focused culture within your organization involves promoting open communication about security concerns (more on this later).
An effective way to foster such a culture is to recognize and reward security best practices, which will motivate employees to adhere to security guidelines. Also, you can use free online training resources and encourage certification in cybersecurity domains to further build a knowledgeable and security-aware team.
4. Implementing Security Controls
As mentioned above, implementing controls like firewalls, anti-malware, and encryption are foundational steps in securing your software.
You must set up access controls and authentication mechanisms to make sure that only authorized individuals can access sensitive systems and data, and administrative controls will establish procedures that guide how security is handled within the organization.
Conducting regular security audits and assessments will help in identifying areas for improvement – which we discuss further below. Through a combination of technical, administrative, and physical controls, a solid security framework can be established to protect against a wide range of cyber threats.
5. Securing Customer Support Channels
Besides, it is crucial to secure customer support channels, particularly contact centers, which are often the hub of customer interaction and data exchange.
Contact centers handle a vast amount of sensitive information, making them a potential target for cybercriminals. By implementing stringent cybersecurity protocols within your contact centers, you ensure an additional layer of defense, safeguarding customer data and maintaining trust.
This includes encryption of communications, regular security training for support staff, and the use of secure, authenticated access to customer service tools and databases.
Evaluating the Effectiveness of Your Cyber Armor
Evaluating the effectiveness of your software security is an essential and ongoing component of making sure your business is safe and secure.
It involves continuous monitoring and updates, regular security audits, and an efficient incident response and analysis procedure. Each aspect is crucial for ensuring that your security measures are not only adequate but also up-to-date with the evolving cyber threat landscape.
Monitoring and Maintenance
Continuous monitoring is essential to keep a close eye on the security posture of your organization. By employing security information and event management (SIEM) protocols to monitor your software security, you can collect and analyze all suspicious activities. This helps to get a comprehensive view of your security landscape, and which types of attacks you need to be most wary of.
Maintenance and updates are another crucial part of ensuring your software security remains effective. Quickly making any software updates or using software patches will help to stay on top of known vulnerabilities, and keeping your security solutions updated to the latest versions ensures that you have the most current protection available.
Regular Security Audits
Regular security audits are a vital part of evaluating the effectiveness of your software security.
Conducting both internal and external audits provides a comprehensive view of your security posture from different perspectives, which helps provide the most information on where your current systems stand.
Once you’ve performed the audit, correctly interpreting these results is essential in order to glean valuable, actionable insights. These insights can then guide actions in adjusting your system accordingly.
Source: DNSstuff
Incident Response and Analysis
Having an established incident response plan is crucial to ensure a structured and effective response to security incidents.
Analyzing security incidents for improvement is a continuous learning process that helps in identifying the weaknesses in your current security setup. Leveraging forensic analysis can provide deeper insights into the incidents, helping to understand the root cause and to prevent similar incidents in the future. This process of incident response and analysis is crucial for refining your software security and enhancing your organization’s resilience against cyber threats.
Future-Proofing Your Business Against Cyber Threats
Cyber threats continue to evolve, and so should your security strategy. Future-proofing your business against these threats involves staying updated on emerging security technologies, engaging with the wider security community, and fostering a culture of security awareness within your organization.
Staying Updated on Emerging Security Technologies
It’s imperative to explore next-gen security solutions to stay abreast of the evolving cybersecurity landscape. The integration of Artificial Intelligence (AI) and Machine Learning (ML) is revolutionizing the security industry by enhancing threat detection, anomaly recognition, and pattern analysis.
These technologies can process vast amounts of data in real-time, identifying potential security threats more accurately and rapidly than human operators. Blockchain technology is also being applied to various security applications due to its decentralized and tamper-resistant nature, which can enhance security in different domains.
It’s important to implement model risk management as the biases and imperfections associated with Artificial Intelligence and machine learning can lead to security issues.
Cybersecurity conferences and expos are platforms to discover innovative solutions and learn about the latest trends in cybersecurity. These venues provide opportunities to network with industry experts and peers, gaining insights that can be applied to improve your cybersecurity posture.
Engaging with the Wider Security Community
Engaging with the wider security community can provide invaluable insights and support.
Participating in security forums and groups like AntiOnline Forums and Reddit’s Netsec community allows for interaction with peers and industry experts, and the exchange of knowledge and experiences. Sharing best practices and lessons learned enhances collective knowledge which can be leveraged to improve cybersecurity measures.
Collaborating on threat intelligence through platforms that provide shared knowledge on emerging threats can also be a proactive approach to understanding and mitigating new cyber threats. Contributing to open source security projects fosters a collaborative spirit in the cybersecurity community and enhances your security posture through collective effort.
Fostering a Culture of Security Awareness
Fostering a culture of security awareness within your organization is crucial for long-term cybersecurity resilience. Encouraging continuous learning and promoting security best practices organization-wide ensures that everyone is aware of their role in maintaining a secure environment.
Engaging in community security initiatives provides an opportunity to learn from others and contribute to the collective security of the wider community. Through these initiatives, not only do you protect your own organization but also contribute to a broader understanding and mitigation of cyber threats.
Conclusion
In a digital age where cyber threats continually evolve, with very real and realistically, crippling consequences, a dynamic, holistic approach towards software security is now an absolute necessity.
Elevating one’s software security calls for a combination of advanced technology, community engagement, and a persistent culture of awareness and education within your business.
As businesses stride forward in this endeavor, the blend of robust security measures and an ongoing commitment to evolving with the cybersecurity landscape both defends the present and also prepares for the future, ensuring a resilient, secure foundation amidst a world of ever-advancing cyber threats.





















Leave a comment!