While world governments have their hands full dealing with the COVID-19 pandemic, shady cyberheist operators are busy working the other way creating a vast fortune, to the tune of $6 trillion by 2021 reckoning alone. If that total amount is a country’s GDP, it’s next only to the income of the US and China.
As technology keeps evolving at a rapid pace, so do cybercrooks. Apart from newer forms of cyber threats, even the oldest tricks in the book are not completely useless for these cybercriminals. They take these tricks out of the box and make modifications and updates to bypass security measures especially created for them. Further in this article, we present the latest cybercrime trends, from data breaches and phishing to cyberactivism and the use of IT security software tools to help you stay in-the-know.

Cybercrime Trends Table of Contents
How to stop criminal activities whose returns far outweigh any fear of punitive actions international institutions have in place? The attempt to cut down cybercrimes is approaching Pyrrhic proportions, with a 15% annual growth rate in returns denting any attempt to throw this bunch of crooks over the cliff. At that rate, they’re even bound to increase their bounties by around $10.5 trillion in 2025.
With all the financial muscle and the best talents in the trade, cybercriminals are increasingly becoming sophisticated too, even using COVID-19 and Medicare messages and phone calls to scam people.
With no end in sight to the rise in cybercrime, there are free IT security solutions that you can try, but investing in IT security can pay off so much more than what it’s worth.
Source: Imperva (2019)
Awareness of how these attacks take form can do wonders. In the following section, we provide a more comprehensive discussion of the latest cybercrime trends affecting various industries for reference.
1. Pandemic-Related Phishing
Phishing has always been prevalent and, at one point, it became the most significant cybersecurity threat in a year. To combat phishing attacks, security companies over the years, kept developing new methods, such as hardware-based authentication and renewed approaches to security-oriented training and awareness, yet phishing is still effective today and many still fall victim to it.
However, recently, it became a critical issue again because of Covid-19. Cybercriminals have been using the pandemic narrative to peddle fear and con individuals to provide them access to sensitive information. One example was recorded in the UK. Elderly people received emails and calls that promised them Covid-19 vaccination as long as they provide the data that the email sender or caller asked (Infosec, 2021).
Another mode of phishing related to the pandemic is a common one. Email recipients would be led to click on links that supposedly offered health advice or policies for remote workers.
Individuals in the US are experiencing something similar as well. Scammers would call people and their numbers would appear as if they originated from the CDC. A great number of these callers would request donations. Additionally, attackers would utilize emails that include links and downloads for malware, which enable them to steal information from victims. One such email campaign even uses the name of CDC to con people (CDC, 2020).
Another tactic has had widespread success. Hackers are imitating a Skype login page and are conning users into providing their usernames and passwords, as they believed they were logging into a legitimate platform. Cybercriminals have been so successful at this because they are aware that 90% of data breaches are caused by human error.
The phishing threat has reached an all-new level. Google’s Threat Analysis Group shared that they blocked 18 million Covid-19 themed emails that contained phishing links and malware downloads per day (Security Magazine, 2020). This is a staggering number of emails that got caught but there are still numerous emails that managed to escape cybersecurity nets. To prevent falling victim to phishing scams, users need to be more vigilant with the links they open and the files they download.

Pandemic-related phishing trends highlights
- Cyberattackers are exploiting the pandemic to victimize people.
- A phishing campaign has been posing as the CDC.
- Google blocked 18 million Covid-19 themed emails per day.
2. Ransomware Attacks
Ransomware remains one of the biggest threats on the web today. First coming into the fore in 2017 with the effects of global campaigns NotPeya and WannaCry, reports show that the number of ransomware attacks doubled in 2018, hitting 10.5 billion globally. In the following year, however, that figure decreased to 9.9 billion (SonicWall, 2020).
Nevertheless, ransomware attacks remain a critical threat to cybersecurity, especially due to the intensive digitization that companies went or are going through because of COVID-19. In 2020, 51% of organizations were hit by a ransomware attack; three-quarters of which resulted in data becoming encrypted. As a result, 26% of victims paid the ransom to get their data back. Unfortunately, 1% of those who did so did not have their data freed and released back to them (Sophos, 2021).
To combat ransomware attacks, there are several decryption tools available in the market, but developers of ransomware see to it that they continue to always be one step ahead by releasing new versions of malware.
Ransomware attacks trends highlights
- 51% of organizations were hit by ransomware attacks in 2020.
- 26% of victims paid the ransom.
- 1% of victims who paid the ransom did not get their data back.
3. Increase in BEC Attacks
The first half of 2020 saw a 200% increase in Business Email Compromise (BEC) attacks (Bitdefender, 2020). The targets of these cyberattacks were businesses that frequently dealt with suppliers abroad and who exchange money online.
To commit this kind of cybercrime, hackers pose as vendors, suppliers, or customers, they are able to hijack money exchanges and redirect those to their own accounts.
An example of a BEC attack happened to a telecommunications provider. The hacker posed as a genuine vendor, successfully persuading employees to direct a payment to a different account. Fortunately, the company’s cybersecurity team detected that a legitimate invoice was being rerouted and stopped the transaction before it went through. If they had not, it would have led to a $700,000 loss to the business (Cloudbric).

Increase in BEC attacks trends highlights
- There was a 200% increase in BEC attacks in the first half of 2020.
- These attacks would target the corporate email accounts of high-level employees.
- Attackers would hijack transactions.
4. Mobile Malware
In the third quarter of 2020, Iran, Bangladesh, and Algeria topped the list of countries with the most mobile malware attacks. The report shows that 30.29% of mobile users in Iran experienced a mobile malware attack. Bangladesh and Algeria follow closely behind, with 17.18% and 16.28%, respectively of mobile users reporting mobile malware (Securelist, 2020). Pakistan, which used to be among the top three countries most afflicted by mobile malware, is no longer even in the top 10.
Like other kinds of cyber threats, mobile malware is also becoming more sophisticated. Last 2020, the Microsoft 365 Defender Research Team uncovered a new Android malware, which was the latest evolution of mobile ransomware and also much more sophisticated than its predecessors. This malware fully disabled the use of Android devices and forced individuals to pay the ransom to gain back control (Microsoft, 2020).
This evolution is not going to halt anytime soon. According to the same research team, more variants are to be expected in the future. This is due mainly to machine learning, which feeds the evolution of malware.
To guard against mobile malware, users have to be more mindful of the websites they visit,m the files they download, and the links they click on. It would also be prudent to install a cybersecurity app to help prevent such attacks.
Source: Kaspersky, 2020
Mobile malware trends highlights
- Iran, Bangladesh, and Algeria are the countries with the most mobile malware attacks.
- Mobile malware is becoming more sophisticated.
- They are continuously evolving with the help of machine learning.
5. Cyberactivism
Cybercrime is no longer just for thieves. Cyberactivists are now also contributing to the vast amount of cybercrimes that happen daily. Modern activist movements consider cyberactivism as a significant milestone. And according to cybersecurity analysts, hacktivism shows no signs of stopping this year and in the years to come.
Cyberactivists are the online equivalents of protesters fighting for a particular agenda. One of their main purposes is to interrupt the website operations of a company or an organization as a way of getting across their messages to the higher-ups. Another motive is to spread awareness about a company’s bad practices.
One such example of cyberactivism is the infamous attack on PayPal and MasterCard. In 2010, a group of cyber activists who claimed to be part of Anonymous executed a DDoS attack on PayPal in response to PayPal’s shutdown of payment services to WikiLeaks. Cyberactivism is expected to grow in the coming years and affect business sales and revenues.
A more recent incident of hacktivism is in relation to the Epstein ring. The group of hackers called Anonymous publicly listed names that were related to Jeffrey Epstein and his clandestine activities. This action was in response to the killing of George Floyd (AS, 2020).
Cyberactivists trends highlights
- Cyberactivism is expected to grow in the coming years.
- Cyberactivism can be a vehicle for desired social change.
- Cyberactivists also contribute to the number of cybercrimes every year.
6. AI and IoT in Cybercrime
AI goes both ways in cyberspace: it can both be a blessing and a curse. With the advent of IoT devices, AI is predicted to commit more cybercrimes than actual people in the year 2040. AI and IoT are gradually making things easier for cybercriminals. Any device that can be connected to the Internet carries the risk of getting hacked. And with the rapid growth of the technological advancements in the AI aspect, IoT devices are facing security issues that seem to have no solutions as of yet.
Even the United Nations Interregional Crime and Justice Research Institute (UNICRI) have begun looking into the advanced understanding of AI applications for criminal justice and crime prevention. But while AI could prevent and deter crimes, the risk lies in the system that can pose a global security threat if left alone with its machine-operated directives.

AI and IoT in cybercrime trends highlights
- AI can open more doors for cybercrime.
- By 2040, there can be more cybercrimes committed by AI than actual people.
- Security issues are prevalent in IoT devices.
7. Supply Chain Attacks
While supply chain attacks are not the most common cybercrime, they are still extremely damaging. These can occur when cybercriminals find a weakness or a number of vulnerabilities in an organization’s ecosystem, particularly through third-party systems. This is fuelled by the sudden surge of digitalization, the rise in remote work, and the growing number of connected devices. Because of these drivers, cybercriminals are able to exploit more entry points in the supply chain (World Economic Forum, 2021).
A most damaging supply chain attack happened to Solar Winds in 2020. The company deals in system management tools that are widely used by IT professionals, the most popular of which is Orion NMS. Hackers exploited the configurations of the software, particularly its integrations. They inserted malware into SolarWinds’s servers, which was packaged as part of an update. This effectively allowed the threat group to get inside the systems of all organizations using Orion NMS, among which are the US Department of Defense and 425 names in the US Fortune 500 (SANS Institute, 2020).
Supply chain attack trends highlights
- Not a common cybercrime but extremely damaging.
- Cybercriminals exploit the vulnerabilities exhibited by third-party systems.
- The biggest supply chain attack so far was initiated through SolarWinds’s Orion NMS.
8. Data Breaches
Data breaches happen daily, and it is one of the biggest cyber threats on the web today. Every year, the number of data breaches continues to increase. Just between January and September 2019, more than 7.9 billion data records were breached. This figure was a 33% increase from 2018.
But while organizations have taken steps to better secure their data, data breach incidents still increased in 2020. In the first quarter of 2020 alone, there was a 273% rise in incidents. From this alone, we can surmise that data breaches are most likely going to continue and may become more damaging in the coming years. (IdentityForce, 2020).
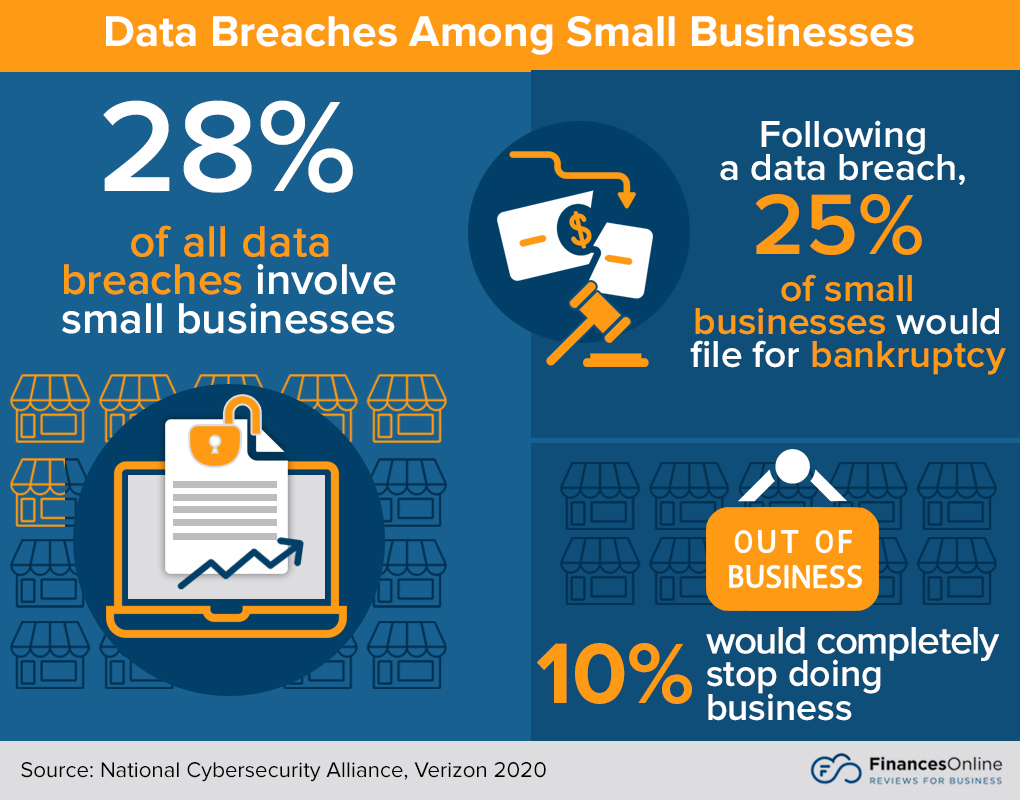
Data breaches trends highlights
- Data breaches in 2019 were a 33% increase from 2018.
- In the first quarter of 2020, data breaches rose to 273%.
- The trend is likely to continue beyond 2021.
9. Cryptojacking
Cryptojacking is threatening ransomware’s position as the most dangerous form of a cyber attack. Malware developed to infect systems to mine for cryptocurrency, cryptojacking is replacing ransomware on the watchlist of cybersecurity analysts. Several studies also show that most recent malware attacks today are designed specifically for cryptojacking, where the malware infects a system with malicious code and then uses its CPU to mine for cryptocurrency.
There are three reasons why cryptojacking will continue to thrive ahead:
- The number of potential targets is in the billions. Many devices are already infected and flying under the radar.
- It’s direct payout for minimal effort. There is no need for additional steps to get money, such as data brokers or via “crypto tumbling,” a process similar to money laundering.
- Cryptojacking is only one step removed from data exfiltration. Once a foothold is established within environments, cryptojacking could easily evolve into wormable malware, piggybacking on advanced techniques. It could also evolve into botnets for hire or data theft.
With cryptocurrency shaping today’s cyber threat environment, mining services and currency exchanges are facing the risk of getting hacked. The ease of cryptojacking and the wide availability of attack tools make cryptomining malware a regular among cybercrime future trends. It is also expected to provide a low-risk revenue stream for cybercriminals.

Cryptojacking trends highlights
- Cryptojacking is a growing threat in cyberspace.
- Cryptomining malware are on their way to become a regular thing in the future
- Cryptojacking creates a low-risk revenue stream for cybercriminals.
Most Popular IT Security Software
- Norton Security. A powerful multi-OS and multi-device software built to provide real-time protection against spyware, viruses, and cyber threats. Read these Norton Security reviews to learn more about this platform’s functionalities.
- Cloudflare. Besides offering content delivery network (CDN) services, Cloudflare is a powerful network security solution. Cloudflare reviews show that this product is apt for protecting SaaS services, mobile apps, APIs, and websites.
- Avira Antivirus Server. A reliable antivirus solution that provides bank-grade protection to business servers. Avira Antivirus Server reviews reveal that ease-of-use and scalability are some of its strong points.
- Malwarebytes. A powerful protection solution designed to provide protection against ransomware, malware, and other cyber threats. Read Malwarebytes reviews to find out more about this product.
- Kaspersky Lab. Arguably the most popular IT security solution designed to provide endpoint security. Read Kaspersky Lab reviews to learn more about its multi-layered security, remote management, and fraud management options.
10. Targeted Attacks
While targeted attacks are not exactly new in the cybercrime scene, it is no less threatening than the existing types of cyberattacks. Targeted threats are crimeware designed for specific industries or corporations, and with its ability to capture sensitive information, it continues to become a major concern for most organizations.
In 2019, the Asia-Pacific region experienced the most targeted cyber attacks in the corporate or internal network (75%). Meanwhile, though Latin America did not suffer much from the same kind of cybercrime (25%), the region’s IT environments were most hurt in the eCommerce sector (75%) (Trustwave, 2020). The following year, it was observed that Brazil was the most targeted country in Latin America for cyberattacks, with 55.97% of users hit by cybercriminals (Mundo en Línea, 2020)
Meanwhile, healthcare companies are emerging this year as one of the industries often targeted by such malware. Newest research by Proofpoint US, a California-based enterprise security solutions provider, found that about 77 percent of phishing emails were targeted the medical sector for the first quarter of 2019. The cybercrime trends in healthcare involved the use of malicious links disguised as regular emails.
Source: Mundo en Línea, 2020
Targeted attacks trends highlights
- The Asia-pacific region had to field the most targeted attacks on corporate infrastructure in 2019.
- Latin America is most hurt by targeted attacks in the eCommerce sector.
- Brazil experienced the greatest share of cyberattacks in Latin America in 2020.
11. Encrypted Communication Platforms
End-to-end encryption is one of the best ways to keep communication between two points anonymous and totally difficult to trace. Thus, there is no wonder as to why cybercriminals decided to shift to encrypted chatting platforms for communication and commerce. With encrypted peer-to-peer chat platforms like Jaber and WhatsApp, it’s harder for law enforcement to decrypt messages and eavesdrop on the plans of cybercriminals.
These instant messaging programs give cybercriminals an advantage. By using such a form of communication, the FBI finds it difficult, if not impossible, to decrypt their messages containing the details of their cybercrime operations. As such, governments are fighting for legal access to the data from tech companies that provide such services. Some examples of these are Apple and Facebook.
Of course, while encrypted messaging has become a go-to for cybercriminals. It’s important to note that many still use mainstream instant messaging apps. Skype, for example, although not encrypted and as secure as other messaging platforms, is still among the most popular and most preferred platforms of cybercrime gangs around the world, according to FlashPoint’s study of communications platforms used by financially motivated cybercriminals.
Encrypted communications trends highlights
- Cybercriminals prefer communicating using encrypted chat messaging platforms.
- Skype is also a popular instant messaging platform that cybercriminals use.
- Encrypted messaging programs give law enforcement a hard time decrypting messages.
12. Bitcoin Popularity
As bitcoin becomes more popular, it’s also amplifying ransomware. Bitcoin has also been reported as one of the most popular ransom payment methods to elude law enforcement. And although other virtual currencies like monero see a growth in interest, bitcoin still tops the list of cryptocurrencies encountered in cybercrime investigations.
The value of bitcoin more than doubled in 2019. In the coming months, it could rally even higher than the $12,902 level in June of the same year. And because of its value, anonymity, and decentralized system, cybercriminals are naturally drawn to it. It became the preferred currency of darknet criminals and thus increased the number of cryptocurrency malware. In 2017, Malwarebytes, an anti-malware software company, reported having to stop 250 million attempts to infect PCs with coin-mining malware in just one month.

Bitcoin popularity trends highlights
- Bitcoin is the preferred currency of darknet criminals.
- The popularity of bitcoin also drives the increase in coin-mining malware.
- In just one month, Malwarebytes had to stop 250 million attempts to infect PCs with coin-mining malware.
13. DDoS Attacks
By overloading a server with a maximum number of junk requests, DDoS attacks can take down even the largest websites. Apart from its number, the sophistication, complexity, and duration of DDoS attacks are also increasing and becoming even more problematic. This is why Norton dubs DDoS attacks are one of the most powerful weapons on the Internet.
For the first time, DDoS attacks breached the 10 million mark for annual attacks in 2020. This figure is almost 1.6 million higher than the 2019 count. An IT security organization observed that the rate of DDoS attacks started increasing in March of 2020, which coincides with the outbreak of the COVID-19 pandemic. During that period, the month of May saw the most attacks with 929,000 recorded. Sectors most affected by these attacks are ecommerce, online learning, healthcare, and broadband providers (NETSCOUT, 2021). The surge in such attacks can also be attributed to the sudden jump in digitization or reliance on online services for business continuity.
DDoS Attacks by the Numbers
Source: NETSCOUT, 2021
Designed byDistributed denial of access attacks trends highlights
- DDoS attacks remain as one of the most powerful weapons on the Internet.
- At the height of the pandemic, the number of DDoS attacks increased dramatically.
- The sectors that were most affected were essential to business and education continuity during the lockdown.
14. Outdated and Open-Source Vulnerabilities
While open-source software are a source of savings, especially for small organizations, they are also a source of vulnerabilities. These are a favorite gateway of cyber attackers and they even crawl the Internet continuously to find those. To mount an attack, cybercriminals fingerprint OSS elements as well as closed-source web software from providers like Microsoft or Oracle. Once they discover the vulnerability, attackers will begin to exploit the systems that run the vulnerable software. To prevent other cybercriminals from doing the same thing, the ones that have entered the system would patch the vulnerabilities.
In 2021, this is a trend that will be seen often, considering that there are many new, cheap software in the market. While they may seem cost-effective, they can hide vulnerabilities like open-source components that can be exploited by cybercrooks easily. Thus, it is important that organizations ensure that they are dealing with vendors that are transparent with the use of open-source elements for active prevention.
Business email compromise trends highlights
- About $12 billion in domestic and international losses are attributed to BEC scams.
- Manufacturing and construction firms are the top targets for BEC fraud.
15. Social Engineering
Social engineering attacks can affect businesses of all sizes, and that is still true in 2019, especially with the amount of trust businesses and individuals place on online communication. Computer-based social engineering, which includes phishing campaigns, baiting, and clicking on malicious links, remains prevalent in today’s highly digital era. Even the best cybersecurity software companies would admit that social engineering in cybercrime is still a major concern.
The percentage of successful social engineering attacks rose from 71 percent in 2015 and 76 percent in 2016 to 79 percent in 2017. Moreover, it takes roughly five months to detect a social engineering attack, which is why it’s one of the most popular methods for data breach. 97 percent use social engineering, while only three percent of data breach attacks involve malware.
Social engineering trends highlights
- In 2017, the percentage of successful social engineering attacks rose to 79 percent.
- It takes about five months before companies detect a social engineering attack.
- Instead of malware, social engineering is used more for data breach.
16. RDP Attacks
Because of the rise of RDPs, this year saw a decline in automated attack toolkits. Designed to exploit vulnerabilities in widely used software, automated attack toolkits are now being replaced by RDP attacks. RDP credentials can give attackers remote access to a corporate environment, which further leads to a network search of intellectual properties or cryptolock systems.
Thus, RDP is now becoming a common method for cybercriminals to gain access to systems and data, with their targets usually small and medium-sized businesses (SMBs). According to Beazley, about 71 percent of ransomware attacks target SMBs, and RDP usually acts as an attack vector to further launch a ransomware attack.

RDP attacks trends highlights
- RDP attacks are replacing automated attack toolkits.
- About 71 percent of ransomware attacks are through RDPs, and their targets are SMBs.
What role does employee training play in preventing cyber threats?
Employee training is crucial in preventing cyber threats, as human error is often a weak link in cybersecurity. Organizations can greatly reduce risks by equipping their employees with the knowledge and tools to identify and respond to cyber threats.
- Recognizing Phishing Attempts: Training employees to spot phishing emails and suspicious links can drastically reduce the likelihood of cyber intrusions. Regular training sessions and simulated phishing exercises can prepare employees to recognize red flags.
- Securing Remote Access: With the rise of remote work, employees must understand how to secure their remote connections and avoid risky behaviors, such as accessing company systems from unsecured networks.
- Password Hygiene: Teaching employees to create strong, unique passwords and encouraging the use of password managers help protect against unauthorized access and brute-force attacks.
- Incident Reporting: Employees should know the correct protocols for reporting security incidents or potential breaches. Early reporting can prevent an isolated issue from escalating into a full-scale attack.
By investing in ongoing cybersecurity training, organizations can foster a culture of security awareness, making employees a strong line of defense against potential cyber threats.
Cybercrime Trends to Watch Out For
As it is with the proverbial coin, there are two sides to cyberspace. Cyberspace is a great place for commerce, societal advancement, and innovation. However, the same place harbors hooks who are ready to pounce any chance they get. Advanced technology and systems give an edge to businesses and organizations, but it means newer and more advanced methods for cybercriminals to attack too, leading to a marked increase in dangerous cybercrime trends.
Cybercrime presents the trickiest types of criminals to deal with. Armed with sophisticated tools of the trade, they are getting more audacious every day, threatening businesses of all sizes. Bigger organizations have deeper pockets for more advanced security tools to face cyber threats, but small business enterprises are not always so lucky. Thus, staying aware and vigilant at all times can go a long way in preventing these cyberattacks from occurring, and it is also helpful to know what IT security solutions are perfect to protect your site.
Key Insights
- Increasing Cybercrime Impact: Cybercrime is expected to cause financial damage amounting to $6 trillion by 2021 and $10.5 trillion by 2025, making it a major global economic threat.
- Pandemic-Related Phishing Surge: The COVID-19 pandemic has fueled a significant increase in phishing attacks, with cybercriminals exploiting public fear and misinformation.
- Ransomware Remains a Major Threat: Ransomware attacks continue to be prevalent, with a significant portion of victims opting to pay the ransom, despite the risk of not recovering their data.
- Rise in Business Email Compromise (BEC): There has been a notable increase in BEC attacks, where cybercriminals hijack business transactions to steal funds.
- Mobile Malware Evolution: Mobile malware attacks are becoming more sophisticated, with a significant number of attacks reported in countries like Iran, Bangladesh, and Algeria.
- Cyberactivism Growth: Cyberactivism is on the rise, with hacktivists using cyber attacks to promote social and political agendas.
- AI and IoT Vulnerabilities: AI and IoT technologies are increasingly being exploited by cybercriminals, with predictions that AI-driven cybercrime will surpass human-driven attacks by 2040.
- Supply Chain Attacks: These attacks, while less common, can be extremely damaging by exploiting vulnerabilities in third-party systems.
- Persistent Data Breaches: Data breaches continue to rise, with significant increases in the number of incidents reported each year.
- Cryptojacking Threat: Cryptojacking, where cybercriminals use malware to mine cryptocurrency, is emerging as a significant threat, offering a low-risk revenue stream for attackers.
- Sophisticated DDoS Attacks: Distributed denial-of-service (DDoS) attacks are becoming more complex and frequent, particularly affecting essential sectors like e-commerce and healthcare during the pandemic.
- Outdated and Open-Source Software Risks: Vulnerabilities in outdated and open-source software are increasingly being targeted by cybercriminals.
- Social Engineering Persistence: Social engineering remains a prevalent method for cyberattacks, particularly through phishing and baiting techniques.
- RDP Attacks on the Rise: Remote Desktop Protocol (RDP) attacks are becoming more common, targeting small and medium-sized businesses for ransomware deployment.
FAQ
- What is the expected financial impact of cybercrime in the coming years? Cybercrime is projected to cause financial damage of $6 trillion by 2021 and could increase to $10.5 trillion by 2025.
- How has the COVID-19 pandemic influenced cybercrime trends? The pandemic has led to a surge in phishing attacks, with cybercriminals exploiting public fear and misinformation related to COVID-19.
- What are ransomware attacks, and how prevalent are they? Ransomware attacks involve cybercriminals encrypting a victim’s data and demanding a ransom for its release. In 2020, 51% of organizations reported being hit by ransomware attacks.
- What is Business Email Compromise (BEC), and why is it significant? BEC attacks involve cybercriminals hijacking business transactions by posing as legitimate vendors or customers. These attacks saw a 200% increase in the first half of 2020.
- Which countries are most affected by mobile malware attacks? Iran, Bangladesh, and Algeria reported the highest number of mobile malware attacks in the third quarter of 2020.
- What is cyberactivism, and how does it impact businesses? Cyberactivism involves hacktivists using cyber attacks to promote social and political agendas, disrupting company operations and spreading awareness about bad practices.
- How are AI and IoT technologies being exploited in cybercrime? AI and IoT devices are increasingly targeted by cybercriminals, with predictions that AI-driven cybercrime will surpass human-driven attacks by 2040 due to their vulnerabilities.
- What are supply chain attacks, and how do they occur? Supply chain attacks exploit vulnerabilities in third-party systems within an organization’s ecosystem. A notable example is the SolarWinds attack, which affected numerous high-profile organizations.
- How common are data breaches, and what is their impact? Data breaches are increasingly common, with a 273% rise in incidents reported in the first quarter of 2020 alone.
- What is cryptojacking, and why is it a growing threat? Cryptojacking involves using malware to mine cryptocurrency on infected systems. It offers a low-risk revenue stream for cybercriminals and is becoming more prevalent.
- What are DDoS attacks, and which sectors are most affected? Distributed denial-of-service (DDoS) attacks overload servers with junk requests, causing outages. The e-commerce, online learning, healthcare, and broadband sectors were most affected during the pandemic.
- Why are outdated and open-source software vulnerable to cyberattacks? These software types often contain unpatched vulnerabilities that cybercriminals can exploit, making them common targets for attacks.
- How does social engineering contribute to cybercrime? Social engineering involves manipulating individuals into divulging confidential information. It remains a prevalent attack method due to its effectiveness in exploiting human error.
- What are RDP attacks, and why are they increasing? RDP attacks exploit Remote Desktop Protocol vulnerabilities to gain access to corporate environments. They are commonly used to deploy ransomware, particularly targeting small and medium-sized businesses.
References:
- AS (2020). Anonymous: Who are They and Why are They Threatening Trump? AS
- CDC. (2020). COVID-19-Related Phone Scams and Phishing Attacks. CDC
- Cloudbric. (2020). Cybersecurity statistics in the first half of 2020. Cloudbric
- IdentityForce. (2020). 2020 Data Breaches: The Most Significant Breaches of the Year. IdentityForce
- Infosec. (2020). Top 9 Cybercrime Tactics, Techniques and Trends in 2020: A Recap. Infosec
- Mundo en Linea. (2020). Kaspersky: Businesses are the main target of cyberattacks in Latin America. Mundo en Linea
- NETSCOUT. (2020). DDoS Attacks in 2020. NETSCOUT
- SANS Institute. (2020). What You Need to Know About the SolarWinds Supply-Chain Attack. SANS Institute
- Securelist. (2020). IT Threat Evolution Q3 2020 Mobile Statistics. Securelist
- Security Magazine. (2020). How Hackers are Using COVID-19 to Find New Phishing Victims. Security Magazine
- SonicWall. (2021). 2021 SonicWall Cyber Threat Report. SonicWall
- Sophos. (2020). The State of Ransomware 2020. Sophos
- Trustwave. (2020). 2020 Trustwave Global Security Report. Trustwave.
- World Economic Forum. (2021). These are the Top Cybersecurity Challenges of 2021. World Economic Forum


























Leave a comment!