Hackers can expose your personal information or even shut down your entire business operations for any number of hours or days. The growing sophistication of these attacks has led various organizations to clamp down on cyber criminals—the back and forth affair defining the cybersecurity trends we’re experiencing today.
Security deficiencies are costing for-profit and nonprofit organizations billions of dollars in losses. Plus, with companies shifting to remote work since the pandemic began, they have become more vulnerable to attacks from hackers. If you are one of them, it follows that you should keep a close watch on the emerging trends in cybersecurity. In this article, we’ll be presenting the top cybersecurity trends and how they have been reshaping Internet privacy and IT security.

Cybersecurity Trends Table of Contents
Cyberattacks are now the fastest growing crime on a global scale. Financial losses from cybercrime exceed the total losses incurred from the global trade of all illegal drugs. Hence, it comes as no surprise that individuals and organizations operating on the web live in fear of potential hacking scenarios and data breaches. Aside from financial losses, such forms of cyber attacks can lead to reputation damage as well. Consumer data, when compromised, can subject businesses to strict regulations and costly settlements.
Half of these cyberattacks are targeting small businesses that usually don’t have sufficient cybersecurity measures to protect themselves from such threats. Based on a 2020 survey, the most common cyber attacks experienced by US companies are phishing (38%), network intrusion (32%), inadvertent disclosure (12%), stolen/lost device or records (8%), and system misconfiguration (5%) (BakerHostetler, 2020).
Most Common Cyber Attacks Experienced by US Companies
Phishing: 38
Phishing
%Network intrusion: 32
Network intrusion
%Inadvertent disclosure: 12
Inadvertent disclosure
%Stolen/lost device or records: 8
Stolen/lost device or records
%System misconfiguration: 5
System misconfiguration
%Source: BakerHostetler, 2020
Designed byThat being the case, companies are actively spending their IT budgets on any of the IT security available. As we see exponential advancements in technology, cybersecurity also evolves and matures in its ability to take down cyber threats and attacks. In the following sections, we’ll delve into the latest trends in cybersecurity and how they are affecting businesses and other organizations.
1. User Awareness
As cyber threats become more aggressive each day, businesses and organizations take major steps to strengthen their security measures. For many establishments, cybersecurity awareness is essential to prevent costly identity theft and network hacks that can destroy any company or individual’s reputation. Apart from implementing firewalls and sophisticated IT protocols, companies now deem it important to augment the capabilities of their IT personnel via seminars and the like. After all, 80% of data breaches can easily be prevented by practicing cyber hygiene (Cyber Observer, 2020).
What drives cybersecurity awareness forward is the growing number of people unaware of most cyberattack methods. A report by Infosec indicates that about 97% of the people in the world cannot identify a phishing email, while 1 in 25 people click such emails, thus, falling prey to cyberattacks (Infosec). Aside from this, cybercriminals now resort to more advanced and high-tech forms of phishing and malware infections.
In turn, cybersecurity awareness could help prevent the onslaught of threats and attacks. Some organizations have started to implement the combined use of web- and classroom-based methods and visual aids for cybersecurity awareness training and promotions. On top of this, companies now create policies focusing on how employees handle and share confidential corporate data.

Key takeaways
- Businesses and other organizations are putting more importance on cybersecurity user awareness.
- About 97% of the people in the world cannot identify a phishing email.
2. Geo-Targeted Phishing Threats
Phishing attacks are currently the most pervasive security threat to the IT sector, with many still falling victim to phishing emails. Since cybercriminals use more advanced methods to create well-executed business email compromise attacks (BEC), phishing emails and malicious URLs remain prevalent on the web, except that they are now highly localized, more personalized, and are geo-targeted.
According to the 2019 Data Breach Investigations Report of Verizon, 32% of the data breaches last year involved phishing activities (NIST 2019). Thus, experts see targeted phishing to become more prevalent in the coming years. It is also important to note that 2020 alone saw more than 60,000 phishing websites and 1 in every 8 employees shares information on a phishing site (Security Boulevard, 2020). That being the case, businesses are starting to adopt and invest in comprehensive security awareness programs. Also, organizations are implementing simulators that can explain and recognize emerging phishing patterns and the modus-operandi of these cyber attackers.
Source: Payments Source
Key takeaways
- Phishing attacks are now highly localized, geo-targeted, and more personalized.
- About 32% of data breaches involved phishing activities.
3. Attacks on the Healthcare Sector
Failing to combat cyber threats in the healthcare sector exposes many individuals and organizations to all sorts of liability and security issues. This led to hospitals and health organizations investing more in cybersecurity. In 2019, the value of the healthcare cybersecurity market was 9.78 billion and this is projected to rise to $33.65 billion by 2027 (GlobeNewswire, 2020). Taking into account the impact of COVID-19 on the healthcare sector, experts predict that the market might reach $125 billion as early as 2025 (Cybersecurity Ventures, 2020).
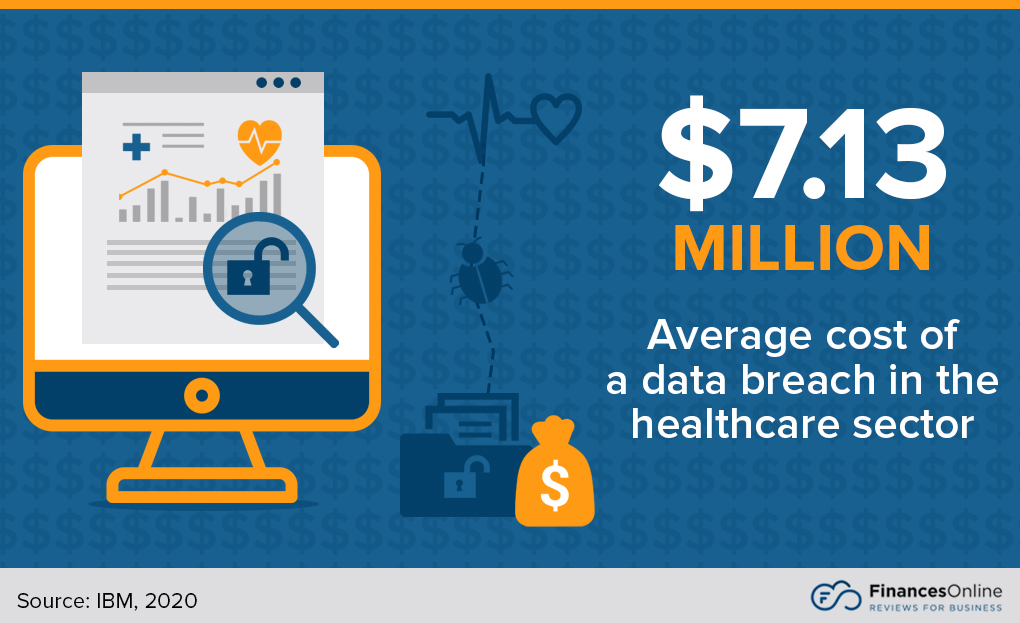
Data breaches are among the leading cybersecurity trends in healthcare. From 2015 to 2019, 157.40 million of healthcare records were exposed (Healthcare, 2020). According to IBM, data breaches like this in the healthcare industry can cost organizations an average of $7.13 million in 2020 (IBM, 2020). As a result, healthcare organizations now pay more considerable attention to their digital security requirements. In turn, this drives considerable growth for the cybersecurity market in the healthcare sector.
However, amid the Coronavirus outbreak, some healthcare organizations temporarily relaxed their firewall rules to make it easier for staff to work from home. Many also needed to expand telehealth services and erect temporary medical facilities that bypassed some of the security diligence protocols of vendors or lacked the usual security infrastructure present in established hospitals.
These figures show that cyberattacks in the healthcare sector are far from being stopped. Data breaches present a continuing threat to health organizations as sensitive information about businesses, employees, and patients remains the top target of cybercriminals. According to a survey by the law firm BakerHostetler, US health systems and hospitals account for about a quarter of cyberattacks in the country.
Key takeaways
- Cyberattacks remain a challenge for those in the healthcare sector.
- The cybersecurity market in the healthcare sector is projected to valued at $125 billion by 2025.
4. Machine Learning
In cybersecurity, the role of machine learning (ML) is growing and has now become more proactive. With ML, cybersecurity becomes simpler, more effective, and, at the same time, less expensive. From a rich dataset, ML develops patterns and manipulates them with algorithms. This way, it can anticipate and respond to active attacks in real-time.
This technology heavily relies on rich and sophisticated data to produce effective algorithms. The data must come from everywhere and represent as many potential scenarios as possible. Implementing ML, thus, allows cybersecurity systems to analyze threat patterns and learn cybercriminals’ behaviors. These help to prevent similar attacks in the future and also reduces the amount of time needed for cybersecurity experts to perform routine tasks.
Key takeaways
- Cybersecurity is adopting machine learning technology to identify attacks and analyze its patterns and algorithms.
- ML makes cybersecurity much simpler and more efficient.
5. Cloud Security
With the help of the best cloud management software solutions, more and more businesses and organizations are migrating to the cloud. However, most cloud services right now do not offer secure encryption, authentication, and audit logging. Some also fail to isolate user data from other tenants sharing space in the cloud. Therefore, IT security professionals see the need to tighten cloud security.
Poor configuration of cloud security can lead to cybercriminals bypassing internal policies that protect sensitive information in the cloud database. Accordingly, security in the cloud is progressing into predictive and innovative security to combat cyber attackers.
Predictive security is becoming useful in identifying threats before attackers begin their move. It can pinpoint attacks that pass through other endpoint security. As a result, businesses are implementing predictive security cloud, with the market gaining a 261% ROI for over three years now (VMWare Carbon Black, 2019). Meanwhile, some sectors have also resorted to leveraging multi-factor authentication to reinforce security.
Businesses that Use Multi-Factor Authentication (MFA)
Technology and software: 37%
Technology and software
37%Education sector: 33
Education sector
%Banking & finance: 32%
Banking & finance
32%nsurance and legal : 20%
nsurance and legal
20%Source: Techrepublic, 2019
Designed byKey takeaways
- Predictive security cloud is now essential to cloud services.
- Predictive security cloud gained a 261% ROI in the last three years.
Top IT Security Software
- Spiceworks Security. A reliable IT management solution that enables IT, professionals, to monitor the status of their network and all devices connected to that network. Our Spiceworks Security review provides in-depth details about this product.
- ManageEngine Firewall Analyzer. An all-in-one configuration management and logs analytics software that helps users monitor firewall policy and understand their internet security better, thanks to the robust reporting function. To find out more, read our ManageEngine Firewall Analyzer review
- Webroot SecureAnwhere. An innovative endpoint security software built to help businesses thwart malware and other forms of cyber threats. Find out more about this solution in our Webroot SecureAnywhere review.
- Bitdefender. A powerful cybersecurity solution designed to help businesses as well as individuals to protect their devices from digital threats. Read our Bitdefender review to find out more about its capability.
- AVG AntiVirus. A powerful antivirus software built to guard organizations against all forms of dynamic, unknown, and advanced cyber threats using an intuitive IT security approach. To learn more about this software, read our comprehensive AVG AntiVirus review.
6. GDPR Compliance
The general data protection regulation, or GDPR, is one of the most significant developments in data privacy regulation across the European Union (EU) nations. But while the law has EU origins, any company that is marketing goods or services to EU residents need to comply with the new regulation regardless of their location. Consequently, GDPR is having an immense impact on global data protection requirements.
GDPR imposes a uniform and consistent data security law on all EU nations. This eliminates the need for each member state to write their data protection law. GDPR, thus, provides more consistent protection of consumer and personal data of EU residents. Although it protects only EU citizens, the law affects all businesses and organizations targeting the European market.
As the law is fairly new, some are still not ready to become GDPR-compliant. As of June 2019, only 28% of companies are able to achieve compliance—a far cry from the 78% of organizations that were hoping to be compliant by 2018 (Help Net Security, 2019). Nonetheless, organizations around the world are gradually applying changes and restructuring to comply with the new law.
How GDPR affected email list among brands partially or fully compliant with the law
Up to 10% decrease in email list size: 41.5%
Up to 10% decrease in email list size
41.5%More than 25% decrease in email list size: 23.8%
More than 25% decrease in email list size
23.8%No effect on email list size: 19.1%
No effect on email list size
19.1%10% to 25% decrease in email list size: 15.6%
10% to 25% decrease in email list size
15.6%Source: Litmus
Designed byKey takeaways
- Businesses targeting the European market are feeling the impact of GDPR.
- About 50% of businesses believe they were already GDPR-compliant by the end of 2018.
7. Threats to Higher Education
Cybersecurity is now among the top priorities of those in the higher education sector, especially with the rise of online learning and remote work in pandemic times. Cybersecurity trends in higher education primarily involve compromised student data. Just this year, three private universities fell victim to a cyberattack that involved the hacking of student admission data (Inside Higher Ed, 2019). This called the attention of those in the higher education sector to actively promote tighter security for the protection of student, faculty, and research data in the institution.
Security Scorecard’s 2018 Education Cybersecurity Report pointed out that in terms of cybersecurity, education comes in last out of the 17 industries in the US (Security Scorecard). Furthermore, the report indicates that the higher education sector is performing poorly in patching cadence, network security, and application security. This is even more alarming as 11% of attacks on US educational institutions are motivated by espionage (Verizon, 2019).
Fortunately, as the number of cyberattacks targeting higher education grows, institutions are now moving towards a new security architecture that includes post-perimeter security on endpoint protection, access to the cloud, and identity information.

Key takeaways
- Cybersecurity is one of the top priorities of the higher education sector.
- Out of 17 industries in the US, the higher education sector comes in last when it comes to cybersecurity.
8. Vulnerability of IoT
Security issues keep plaguing most IoT devices dominating the market today. Computing devices embedded in IoT products allow for sending and receiving data over the Internet. This poses significant security threats to users, exposing them to cyberattacks like DoS or hijacked devices. As IoT connects the virtual space and the physical world, home intrusions are adding to the list of the scariest possible threats that IoT brings. In fact, a report by Symantec reveals that infected routers accounted for 75% of all IoT attacks that occurred in 2018, whereas connected cameras accounted for 15% of them (Symantec, 2019).
As such, IoT devices are presenting vast opportunities for businesses and cybercriminals alike. Despite the ongoing threats, the Boston Consulting Group’s marketing analysis indicates that enterprises are still on their way to invest more than $267 billion in IoT tools in 2020 (Forbes). This is in line with a more recent report that showed the education industry spent 11.9% more on IoT in 2020 than in the previous year (Help Net Security, 2020).
Source: Help Net Security, 2020
Key takeaways
- Most IoT devices in existence today are prone to many cybersecurity issues.
- Infected routers account for 75% of all IoT attacks that occurred in 2018.
9. Mobile Devices as Attack Vectors
These days, nearly everyone uses smart mobile devices—66.6% of the world population as of 2021, to be specific (DataReportal, 2021). Most leading ecommerce software and platforms are accessible through mobile platforms. Cybercriminals, however, see this as an opportunity to target mobile users and use mobile devices as attack vectors.
Mobile devices are becoming a great channel of opportunity for cybercriminals as users continue to use their mobile devices for personal and business communications, as well as banking, shopping, flight, or hotel bookings. These devices became targets of cyberattacks. According to the RSA’s 2019 Current State of Cybercrime whitepaper, about 70% of fraudulent transactions originated from mobile platforms, with popular mobile attack vectors including malware, data tampering, and data loss (RSA, 2019).

Key takeaways
- Mobile devices are popular attack vectors for cybercriminals.
- About 70% of fraudulent transactions occurred through mobile channels.
10. Financial Services Cyberattacks
The financial services sector is another industry facing cyber threats daily. It also doesn’t help that some financial organizations are still struggling to keep pace with cloud migration and the increasing number of regulations. Phishing attacks remain prevalent in the financial services sector, but it’s no longer just via emails. Phishing through social media and other messaging platforms is now among the cybersecurity trends in financial services.
Aside from phishing attacks, the most common threats faced by insurance companies, banks, and asset managers include malware attacks and data breaches. A report by Boston Consulting Group revealed that financial services firms are 300 times more prone to cybersecurity attacks than businesses in other industries (BCG, 2019). Moreover, cyber attacks on financial institutions spiked by a massive 238% from the beginning of February to the end of April 2020 amid the COVID-19 pandemic (Infosecurity Magazine, 2020). Attacks now cost the banking industry $18.3 million per enterprise (Security Boulevard, 2020).
Source: CB Insights
Key takeaways
- Businesses in financial services are more prone to cyberattacks than other industries.
- Attacks on financial institutions spiked by a massive 238% during COVID-19.
- Attacks now cost the banking industry $18.3 million per enterprise.
The Role of Cyber Insurance in Business Security
Cyber insurance is increasingly vital for businesses to protect themselves against the financial fallout from cyberattacks. It offers several key benefits:
- Financial Protection: Cyber insurance covers costs related to data breaches, ransomware attacks, and other cyber incidents, including legal fees, data recovery, and public relations efforts to manage the crisis.
- Business Continuity: Beyond immediate financial relief, it helps companies maintain operations by covering expenses like system restoration and lost revenue due to downtime.
- Incentivizing Security Measures: Insurance providers often offer lower premiums for businesses with strong cybersecurity practices, such as multi-factor authentication and regular audits. This encourages firms to invest in robust security frameworks.
- Risk Assessment and Management: Many insurers perform risk assessments to identify vulnerabilities, helping businesses address weaknesses before they become problems. This proactive approach can prevent breaches and ensure adequate coverage.
- Adapting to Emerging Threats: As cyber threats evolve, so does cyber insurance. Policies are being updated to cover new risks, like ransomware-as-a-service and attacks on remote workforces, providing businesses with continued protection.
Cyber insurance is an essential part of modern cybersecurity strategies. It offers both financial protection and a proactive approach to safeguarding against digital threats.
Developments in the Cybersecurity Arena
No one exactly knows what the future holds for the cybersecurity arena and many sectors are still figuring out how to fortify their networks in the middle of the chaos and uncertainties of the pandemic. But these latest trends provide us with insights into what we can expect in the years to come. What’s clear is that IT security software developers and admins would be busy for years to come.
Sure, popular ecommerce platforms make it easy for businesses to establish their shops online. However, they expose many people to security threats too. Attacks like phishing, malware, and data breaches will not end soon. It gets harder to keep cybercriminals down. When it happens, they usually display resilience, getting back with a vengeance using more advanced types of attacks.
With most businesses establishing their operations in cyberspace, a tight security system is not just an option—it is a must-have if you want to ensure fool-proof protection for your company and your consumers. Identifying critical attack areas and anticipating possible attack scenarios can help you avoid becoming a victim of such attacks. And in case you’re looking for the perfect security software for your company, we compiled the best IT security software companies currently available.
Key Insights
- Cybersecurity Awareness:
- Businesses prioritize user awareness to prevent data breaches.
- About 97% of people globally cannot identify phishing emails.
- Geo-Targeted Phishing Threats:
- Phishing attacks are increasingly localized, personalized, and geo-targeted.
- 32% of data breaches involved phishing activities.
- Healthcare Sector Attacks:
- Cybersecurity in healthcare is a growing market, projected to reach $125 billion by 2025.
- Data breaches in healthcare can cost organizations an average of $7.13 million.
- Machine Learning in Cybersecurity:
- Machine learning enhances cybersecurity by analyzing threat patterns and reducing response times.
- ML makes cybersecurity simpler, more efficient, and cost-effective.
- Cloud Security:
- Predictive security cloud is essential for identifying threats and ensuring data protection.
- Businesses using multi-factor authentication are seeing increased security.
- GDPR Compliance:
- GDPR affects global businesses targeting the European market, enforcing consistent data protection laws.
- About 50% of businesses believed they were GDPR-compliant by the end of 2018.
- Threats to Higher Education:
- Higher education is vulnerable to cyberattacks, with compromised student data being a primary concern.
- The sector performs poorly in patching cadence, network security, and application security.
- Vulnerability of IoT:
- IoT devices are prone to significant cybersecurity issues, with infected routers accounting for 75% of IoT attacks.
- Despite threats, businesses continue to invest heavily in IoT.
- Mobile Devices as Attack Vectors:
- Mobile devices are popular targets for cybercriminals, with 70% of fraudulent transactions originating from mobile platforms.
- Financial Services Cyberattacks:
- The financial services sector is highly prone to cyberattacks, costing the industry $18.3 million per enterprise.
- Attacks spiked by 238% during the COVID-19 pandemic.
FAQ
- What are the most common cyberattacks faced by businesses? Phishing, network intrusion, inadvertent disclosure, stolen/lost devices, and system misconfiguration are the most common cyberattacks experienced by businesses. Phishing remains the most pervasive, accounting for 38% of the attacks.
- How can businesses improve their cybersecurity awareness? Businesses can improve cybersecurity awareness by conducting regular training sessions, seminars, and using both web-based and classroom-based methods. Implementing policies on handling and sharing confidential data also helps in raising awareness.
- Why is the healthcare sector a prime target for cyberattacks? The healthcare sector is targeted because it holds sensitive information about patients, businesses, and employees. Data breaches can lead to significant financial losses and liability issues, prompting increased investments in cybersecurity.
- What role does machine learning play in cybersecurity? Machine learning helps in identifying attack patterns and predicting potential threats. It enables real-time responses to active attacks, making cybersecurity measures more effective and efficient.
- Why is cloud security important for businesses? Cloud security is crucial because poor configuration can lead to data breaches and cyberattacks. Predictive security measures help identify threats before they occur, ensuring better protection for sensitive information stored in the cloud.
- How does GDPR impact global businesses? GDPR enforces consistent data protection laws across EU nations, affecting any business targeting the European market. It requires businesses to comply with strict data security regulations to protect consumer information.
- What cybersecurity challenges does the higher education sector face? The higher education sector struggles with compromised student data, poor network and application security, and low patching cadence. The rise of online learning and remote work has made the sector more vulnerable to cyberattacks.
- Why are IoT devices vulnerable to cyberattacks? IoT devices often lack robust security measures, making them susceptible to attacks like DoS or hijacking. Infected routers and connected cameras are common targets, posing significant risks to users.
- What makes mobile devices attractive targets for cybercriminals? Mobile devices are widely used for personal and business activities, including banking and shopping. This extensive usage makes them attractive targets for cybercriminals, with a high percentage of fraudulent transactions originating from mobile platforms.
- How have cyberattacks on financial services evolved during the COVID-19 pandemic? Cyberattacks on financial services spiked by 238% during the pandemic, with phishing, malware attacks, and data breaches being the most common threats. The increased reliance on digital platforms and cloud migration has made the sector more vulnerable.
References:
- BakerHostetler. (2020, April). 2020 Data Security Incident Response Report. BakerHostetler.
- Cyber Observer. (2020, March 8). 29 must-know cybersecurity statistics for 2020. Cyber Observer.
- Dimov, I. (2017, August 29). Security awareness statistics. Infosec.
- Widdup, S. (2019). 2019 Verizon Data Breach Investigations Report. NIST.
- Meharchandani, D. (2020, December 7). Staggering phishing statistics in 2020. Security Boulevard.
- Fior Market Research LLP. (2020, September 30). Global healthcare cyber security market is expected to reach USD 33.65 billion by 2027: Fior Markets. GlobeNewswire.
- Morgan, S. (2020, September 8). Healthcare industry to spend $125 billion on cybersecurity from 2020 to 2025. Cybercrime Magazine.
- Seh, A. H., Zarour, M., Alenezi, M., Sarkar, A. K., Agrawal, A., Kumar, R., & Ahmad Khan, R. (2020). Healthcare data breaches: Insights and implications. Healthcare, 8(2), 133.
- IBM. (2020, July 29). IBM report: Compromised employee accounts led to most expensive data breaches over past year. IBM.
- VMware Carbon Black. (2019, February 5). New total economic impact study finds CB predictive security cloud delivers 261% return on investment (ROI). VMware Carbon Black.
- Help Net Security. (2019, September 28). Companies vastly overestimating their GDPR readiness, only 28% achieving compliance. Help Net Security.
- Jaschik, S. (2019, March 11). Three private colleges have admissions files hacked. Inside Higher Ed.
- SecurityScorecard. (2018). 2018 education cybersecurity report. SecurityScorecard.
- Verizon. (2019, May 7). Data breaches in educational services. Verizon.
- Davis, D. B. (2019, April 4). ISTR 2019: Internet of things cyber attacks grow more diverse. Symantec.
- Columbus, L. (2017, January 9). Internet of Things market to reach $267B by 2020. Forbes.
- Help Net Security. (2020, June 18). Global IoT spending dropping significantly in 2020, but expected to rebound in 2021. Help Net Security.
- DataReportal, Hootsuite, & We Are Social. (2021, January). Global digital overview. DataReportal.
- RSA. (2019). 2019 current state of cybercrime. RSA.
- BCG. (2019, June 20). For wealth managers, off year sparks opportunity to reignite growth. BCG.
- Muncaster, P. (2020, May 15). Attacks on banks spike 238% during #COVID19 crisis. Infosecurity Magazine.
- Singha, R. (2020, December 19). Banking industry faces surge in cyber security challenges. Security Boulevard.

























Leave a comment!