According to recently published data from Check Point Research, the number of significant cyber attacks impacting established businesses increased by almost 40% globally between 2021-2022, driven by agile hackers targeting teams working within hybrid and remote roles.
As more businesses pivot towards the use of digital communication and collaboration tools to improve workflows and address the needs of modern clients, the threat of sophisticated cyber-attacks continues to rise, with data breaches of particular concern to small companies.
Verizon’s 2021 Data Breach Investigations report found that 46% of all reported breaches impacted small-medium-sized businesses, with data from IBM finding 82% of ransomware attacks in the same year were targeted towards companies with less than 1000 employees.
With the latest IBM Data Breach Report finding 83% of organizations experienced multiple breaches during 2022, it’s clear that small businesses must develop appropriate software solutions and data protection policies if they’re to mitigate the impact of sophisticated cyber attacks. To assist employers, below is a small business guide to accounting data protection.

The importance of accounting data protection
As small businesses will typically find themselves in the possession of personally identifiable information (PII) pertaining to their clients, systems must be in place to ensure this data does not become compromised during transit. Accountants in particular are likely to handle a large amount of sensitive PII when performing essential duties, with common examples including:
- Names / contact information
- Social security numbers (SSN)
- Taxpayer identification numbers
- Financial account numbers
- Credit card details
- Personal addresses / telephone numbers
- Digital asset information
If this data is intercepted by hackers and used to commit acts of fraud or identity theft, clients may suffer financial losses and damage to their personal reputations, with small businesses potentially becoming liable for damages if adequate protection measures were not in place.
In addition, small businesses must ensure compliance with government and industry-specific regulations regarding data protection and the safe handling of PII. US data protection laws have been strengthened in recent years to account for novel technologies and processes, so small businesses must frequently review active policies to ensure systems remain compliant.
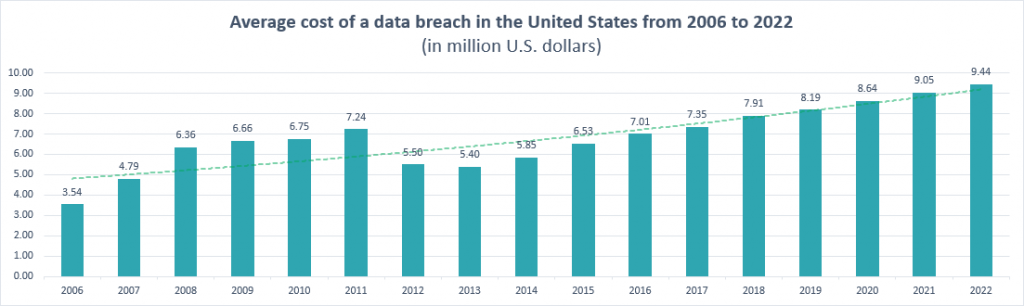
The cost of a data breach
As the number of reported data breaches continues to increase, so too does the estimated cost of significant cyber attacks for small business owners. According to figures published by Statista, the average cost of a data breach targeted towards businesses in the US amounted to almost $9.5 million in 2022, with figures steadily rising year-on-year over the last decade.
As a result of these figures, it’s estimated that 51% of organizations are planning to upgrade existing physical and cyber security systems to better protect sensitive PII, with businesses focusing on employee training, threat detection and incident response tools. To aid business owners in achieving this, below we’ll discuss how to protect small business accounting data.
Data protection tips for small businesses
Developing effective data protection measures for small business accounting information will require teams to assess both physical and cyber security systems to ensure sensitive data is obscured from intruders. To begin, teams must implement smart physical security measures.
Physical security
Managed access control systems must be installed to prevent unauthorized entry to secure locations. Main entrances and exits should only be accessible using company-issued and traceable ID cards, with high-security areas further protected behind advanced credentials.
Server rooms, file storage areas and security offices must be secured using access control locks requiring multi-factor authentication (MFA). Alongside ID cards, biometric scans and one-time passcodes may be utilized to strengthen access security, with security personnel able to monitor the issuing and use of active credentials to improve incident response times.
Video security cameras must also be installed to cover all access points and high-risk areas, with cloud-based systems enabling teams to view footage and receive alerts in real-time. AI video analytics software may also be used to autonomously monitor key locations in search of suspicious activity, alerting security personnel in real-time if a potential threat is detected.
Cyber security
Alongside physical security systems, small businesses must develop comprehensive cyber security solutions used to protect confidential data from external threats. Networks should be secured using frequently updated firewall applications, alongside antivirus and antimalware software used to prevent cyber attacks and malicious files from infecting internal systems.
“A zero trust policy should also be implemented to reduce the number of individuals able to access confidential data,” says Zachary Jarvinen, Vice President of Exact Payments. Zero trust architecture ensures all attempts to access data using internal or external devices are subject to verification checks, meaning all accounts will be asked to provide credentials each and every time the user requests access to information.
In addition to the above mentioned cyber security measures, small businesses must adhere to a several wider cyber security best practices to protect PII from data breaches, including:
- End-to-end encryption – All company-owned devices including desktops, laptops, phones and tablets must be encrypted to ensure data is unreadable if devices are lost or stolen, all communications sent between devices should also be encrypted
- Ban personal devices – Employees should not be permitted to download or view sensitive client information on personal devices, in fact, small businesses should implement an outright ban on using personal devices to access company systems
- Password protections – Access to private systems and databases must be secured behind passwords containing 14+ characters, a combination of upper and lower case letters, numbers and symbols, passwords must also be unique to different systems
- MFA – Access to sensitive systems and databases must be subject to MFA practices, biometrics may be deployed using company-owned smart devices, or one-time codes sent via encrypted messages, experts claim MFA may prevent up to 99% of attacks
- Data disposal policies – Plans must be in place to wipe and destroy all computers, hard drives, USB sticks, CDs and smart devices before these items are disposed of, policies must be written down and frequently reviewed to ensure ongoing compliance
- Data backup protocols – An automated data backup system should be developed to ensure all sensitive PII and important business data is frequently copied and stored in an encrypted server, access to these systems should be restricted to security staff
Employee training
For physical and cyber security solutions to remain effective, small businesses must invest in frequent staff training programs to ensure employees understand accounting data protection best practices and are updated with any new information regarding exploits or vulnerabilities.
Verizon’s 2023 Data Breach Investigations Report found that 74% of recorded data breaches involved the human element, including employees falling victim to social engineering attacks, as well as cases involving the misuse of information and instances of avoidable human error.
All members of staff expected to process PII or access systems used to store sensitive data, such as accounting, security and administrative employees, must attend frequent information security training sessions to receive updated guidance regarding best practises, including:
- Social engineering – Staff must be aware of how to spot and avoid phishing attacks, suspicious emails and malicious links, staff should never open embedded links or attachments associated with unverified sources and avoid sites with no SSL security
- Wi-Fi security – Staff must never connect to any public or unsecured Wi-Fi networks using company-owned devices, or log into company accounts from personal devices connected to unverified Wi-Fi networks, zero trust policies will help to enforce this
- Password hygiene – Employees should be trained in how to select, manage and maintain strong passwords, including rules such as never using the same password for multiple accounts and never including personal information in chosen passwords
- Software updates – Staff in charge of software systems like payroll and accounting solutions must ensure these systems are frequently updated to protect data from new exploits and attacks, even automatic updates should be manually verified by admins
- Disaster recovery – Employees and security teams should work together to develop step-by-step plans detailing how to respond to data loss events, staff must know how to protect data backup systems and prevent attackers from infiltrating wider systems
- Automatic timeouts – All computer systems and accounts should be programmed to automatically lock after a short period of inactivity to ensure that unattended devices do not become susceptible to opportunistic hackers or unauthorized intruders
Summary
As the frequency and severity of cyber attacks and data breaches continue to increase, business owners and security teams across all industries must commit to strengthening existing defenses to prevent sensitive information from being stolen by malicious actors.
Improving data protection measures is of particular importance to small businesses, with reports indicating breaches affect these organizations disproportionately, meaning teams working with sensitive client information must be well-prepared to identify and address threats promptly and efficiently if they’re to protect their clients from fraud and identity theft.
Businesses must adhere to accounting data protection best practices, such as implementing advanced password protections, MFA policies, zero trust protocols and encryption services, as well as commit to strengthening physical security systems and providing frequent staff training programs. By following the advice covered in this guide, small businesses should be well-positioned to improve existing security practices to better protect PII from novel threats.






















Leave a comment!